Web Security Web applications are the cornerstone of modern businesses but are often targeted by attacks like SQL injection, cross-site scripting (XSS), and more. Our web security services include detailed vulnerability assessments, penetration testing, and code reviews to secure your applications against these threats.
By employing the latest security practices, including secure coding standards and regular patch management, we help you protect your web applications and maintain user trust.
Steps We Take: We conduct automated scans, manual penetration tests, and enforce secure coding practices to eliminate vulnerabilities.
IoT Security The rapid growth of IoT (Internet of Things) devices has revolutionized industries and homes alike, creating a seamlessly connected world. However, this connectivity comes with significant security challenges. IoT devices often have weak authentication mechanisms, lack encryption, and run outdated firmware, making them prime targets for cyberattacks.
Our IoT security solutions focus on addressing these vulnerabilities by implementing robust authentication protocols, secure firmware updates, and end-to-end encryption. We also perform comprehensive penetration testing to ensure your IoT infrastructure is resilient against emerging threats. Protect your IoT ecosystem with our expert services.
Steps We Take: We identify weak points through device testing, ensure firmware is updated securely, and implement encryption to protect communication between devices.
Network Security In today’s digital age, securing your network infrastructure is non-negotiable. Cybercriminals exploit unsecured networks to steal sensitive data, disrupt operations, and compromise systems. Our network security solutions provide a multi-layered defense strategy, including firewalls, intrusion detection systems, and advanced threat management.
We also conduct regular vulnerability assessments and network penetration tests to identify and mitigate risks proactively. Safeguard your organization’s digital backbone with our cutting-edge network security services.
Steps We Take: We assess network configurations, deploy intrusion detection systems, and continuously monitor for threats to mitigate risks effectively.
ICS Security Industrial Control Systems (ICS) are critical to operational technology environments, from manufacturing plants to energy grids. Unfortunately, these systems are increasingly targeted by sophisticated attackers. Our ICS security solutions are tailored to protect these essential systems from cyber threats.
We offer real-time monitoring, threat detection, and incident response services, ensuring uninterrupted operations and compliance with industry standards. Trust us to secure your ICS infrastructure effectively.
Steps We Take: We implement robust monitoring systems, perform vulnerability scans on ICS devices, and establish incident response protocols to ensure operational continuity.
API Security APIs are essential for connecting applications but can expose sensitive data if not secured properly. Our API security solutions ensure that your APIs are protected against attacks such as unauthorized access, data breaches, and DDoS attacks.
We provide thorough API assessments, implement authentication mechanisms like OAuth, and apply rate limiting to secure your APIs without compromising performance. Let us safeguard your APIs and ensure seamless and secure integration.
Steps We Take: We test API endpoints, enforce authentication protocols, and deploy rate limiting to prevent misuse and secure integration.
Mobile Security Mobile devices are indispensable in today’s world, but they also introduce unique security risks. From malware to phishing attacks, mobile threats can compromise your data and privacy. Our mobile security services cover application testing, device management, and secure configuration to protect your devices and apps.
We ensure compliance with mobile security standards and safeguard sensitive information against emerging threats. Keep your mobile ecosystem secure with our expert guidance.
Steps We Take: We perform static and dynamic analysis of mobile apps, configure secure device policies, and implement app sandboxing to prevent breaches.
Forensics In the aftermath of a cyber incident, timely and accurate forensics is crucial. Our digital forensics team specializes in identifying, analyzing, and mitigating security breaches. Using state-of-the-art tools, we trace the origin of attacks, recover critical data, and provide actionable insights.
Our services help you build a robust incident response plan and strengthen your defenses against future threats. Trust us to deliver reliable forensic services when it matters most.
Steps We Take: We collect digital evidence, analyze logs, and reconstruct events to identify the root cause of incidents and mitigate future risks.
Thick Client Security Thick client applications, often used in enterprise environments, require specialized security assessments to address their unique vulnerabilities. Our services include reverse engineering, application testing, and secure configuration to protect against threats targeting thick client systems.
Ensure your thick client applications are resilient against exploits with our comprehensive security solutions.
Steps We Take: We analyze client-server communications, identify weaknesses through reverse engineering, and apply patches to secure thick client applications.
Cloud Security As organizations migrate to the cloud, ensuring the security of cloud environments is paramount. Our cloud security solutions cover everything from identity and access management to data encryption and compliance audits.
We work with major cloud providers like AWS, Azure, and Google Cloud to deliver tailored security strategies that protect your cloud infrastructure against breaches and data loss. Secure your cloud journey with confidence.
Steps We Take: We configure secure access controls, monitor cloud environments, and implement encryption to safeguard cloud resources.
Infrastructure Security Your organization’s physical and virtual infrastructure forms the foundation of your operations. Our infrastructure security services include endpoint protection, server hardening, and monitoring to safeguard against internal and external threats.
By deploying advanced security tools and techniques, we help you maintain a secure and reliable infrastructure environment.
Steps We Take: We harden endpoints, secure server configurations, and set up continuous monitoring to detect and respond to threats.
Hardware Testing Hardware vulnerabilities can compromise the security of entire systems. Our hardware testing services identify potential flaws in devices, including embedded systems and IoT hardware.
Through rigorous testing and validation, we ensure that your hardware meets the highest security standards. Protect your devices and systems with our specialized hardware security services.
Steps We Take: We perform physical inspections, firmware analysis, and stress testing to uncover and address hardware vulnerabilities.
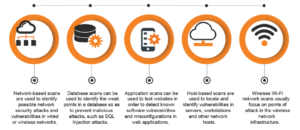
Scanners Used
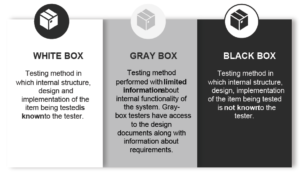
Methods Used
Tools Used



